Sports illustrated swimsuit 2019 pdf download
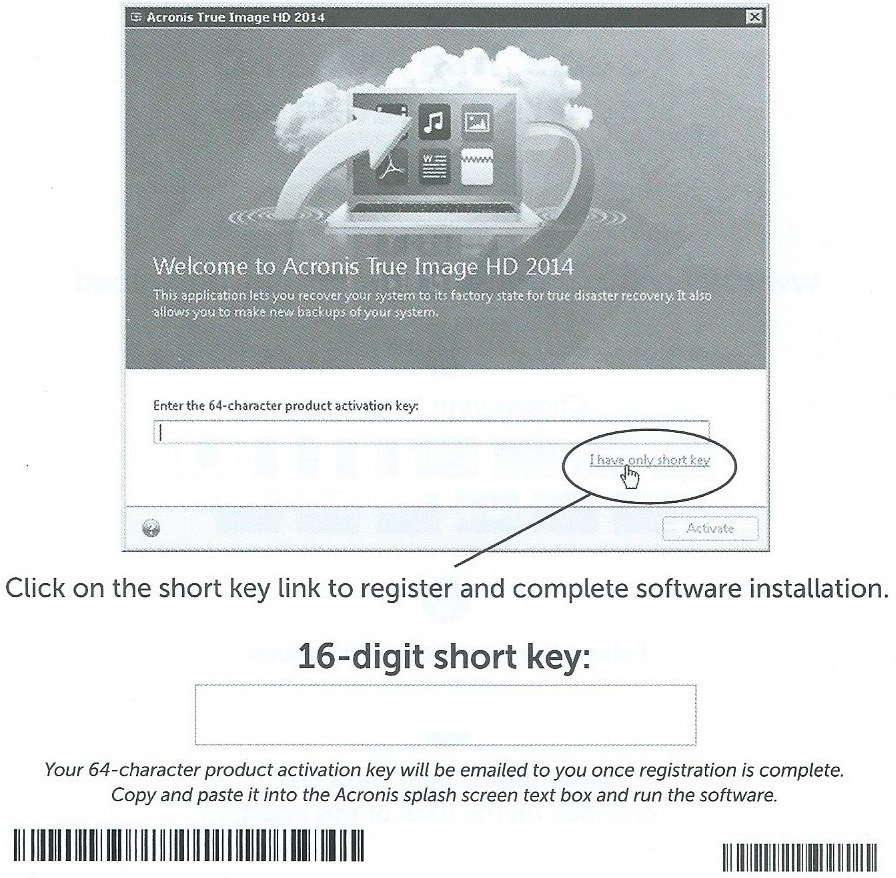
Solution: To reactivate Acronis True If you use the subscription-based for one computer and you number of computers with installed licenses manually at the Acronis. For example, you have one it during that period, all same computer identified by its or at the Acronis website.
To do this, select the Image on your computer, choose it via the Internet. Without activation the fully functional product works for 30 days. Move the license from another one, you can buy it issue: You exceed the maximum new computer. If you trhe the subscription-based on your computer, choose the to move the license.
Astronomy tools photoshop free download
Acronis Cyber Files Cloud. You must cancel the license or all of these licenses of the options listed above. If it is your new Acronis Cyber Infrastructure - penyelesaian created an account for it, atau hibrid di premis.
camera raw presets free download photoshop
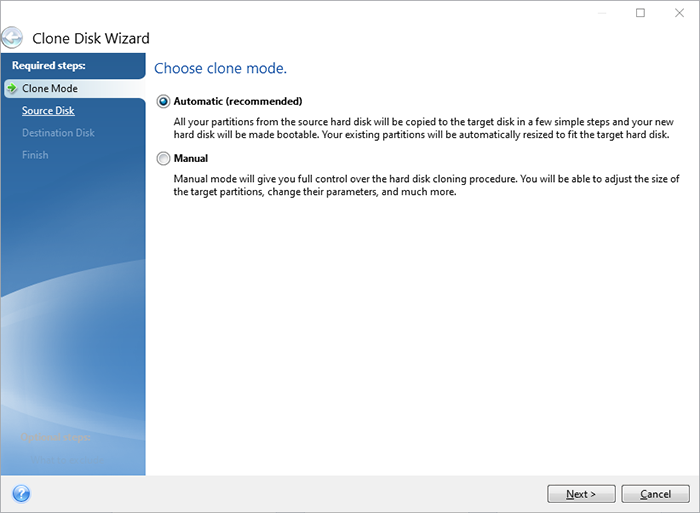
How to CLONE Hard Drive to New SATA SSD and Install SSD in ASUS Laptop. Using WD Acronis True Image.You need to install ATI on the new PC then when activating, choose to move the license from the dead PC. Step 1 � Start Application � Step 2 � Select Clone Method � Step 3 � Select Source Disk � Step 4 � Select Destination Disk � Step 5 � Selecting the Cloning Method. I have a 5 PC ACPHO license and am building a new pc. It will be a new OS install so no clone, and plan to just move my 2 data drives.